SCIM provisioning overview
Testomat.io supports SCIM (System for Cross-domain Identity Management), which allows you to automate your team’s provisioning and de-provisioning. You can use Testomat.io at scale across your organization and control access to it with your identity provider.
This guide shows how to set up user management via SCIM provisioning for various identity providers.
What is SCIM provisioning?
Section titled “What is SCIM provisioning?”SCIM (System for Cross-domain Identity Management) is an open standard that facilitates the automation of user provisioning and de-provisioning between identity providers (IdPs) and service providers. By implementing SCIM, Testomat.io enables seamless integration with various IdPs, allowing for efficient user management.
SCIM features
Section titled “SCIM features”Testomat.io’s SCIM implementation supports the following provisioning features:
User provisioning
Section titled “User provisioning”- Create User: Automates the creation of new user accounts in Testomat.io when users are assigned in your identity provider. New users are automatically added to your company and can be assigned to default projects.
-
Update User Information:
-
Update User Attributes: Modifies user details such as name and email address.
-
Activate User: Creates and activates a new user account if one does not already exist.
-
Deactivate User: Removes a user from the system and deactivates their account, preventing authentication. This is a soft delete operation that preserves the user record. Please note: User accounts and the data corresponding to them won’t be deleted.
-
Reactivate User: Reactivates a previously deactivated user account, restoring authentication capabilities.
-
-
Set User Roles: Assigns roles to users using the Testomat extension schema. Supported roles include:
qa- Quality assurance role (default)manager- Manager rolebilling- Billing administrator roleread- Read-only access status
Group provisioning
Section titled “Group provisioning”-
Create Group: Establishes new user groups (teams) within Testomat.io based on group assignments in your identity provider.
-
Delete Group: Removes user groups from the system.
-
Update Group Information:
- Update Group Attributes: Changes group names and other attributes.
- Update Group Members: Adds or removes users from groups as needed.
Prerequisites
Section titled “Prerequisites”Before enabling SCIM provisioning, ensure the following:
- You have a company in Testomat.io, and you are owner of this company.
- Company is on an Enterprise plan.
- You have configured Single Sign-On (SSO) in Testomat.io. SSO must be configured before you can enable SCIM.
- Your identity provider supports SCIM 2.0 protocol (e.g., Okta, Microsoft Entra ID, OneLogin).
- You have administrative privileges in both Testomat.io and your identity provider.
Enabling SCIM provisioning
Section titled “Enabling SCIM provisioning”You must configure SSO in Testomat.io before you can enable SCIM for your Testomat.io team.
Enabling SCIM in Testomat.io
Section titled “Enabling SCIM in Testomat.io”-
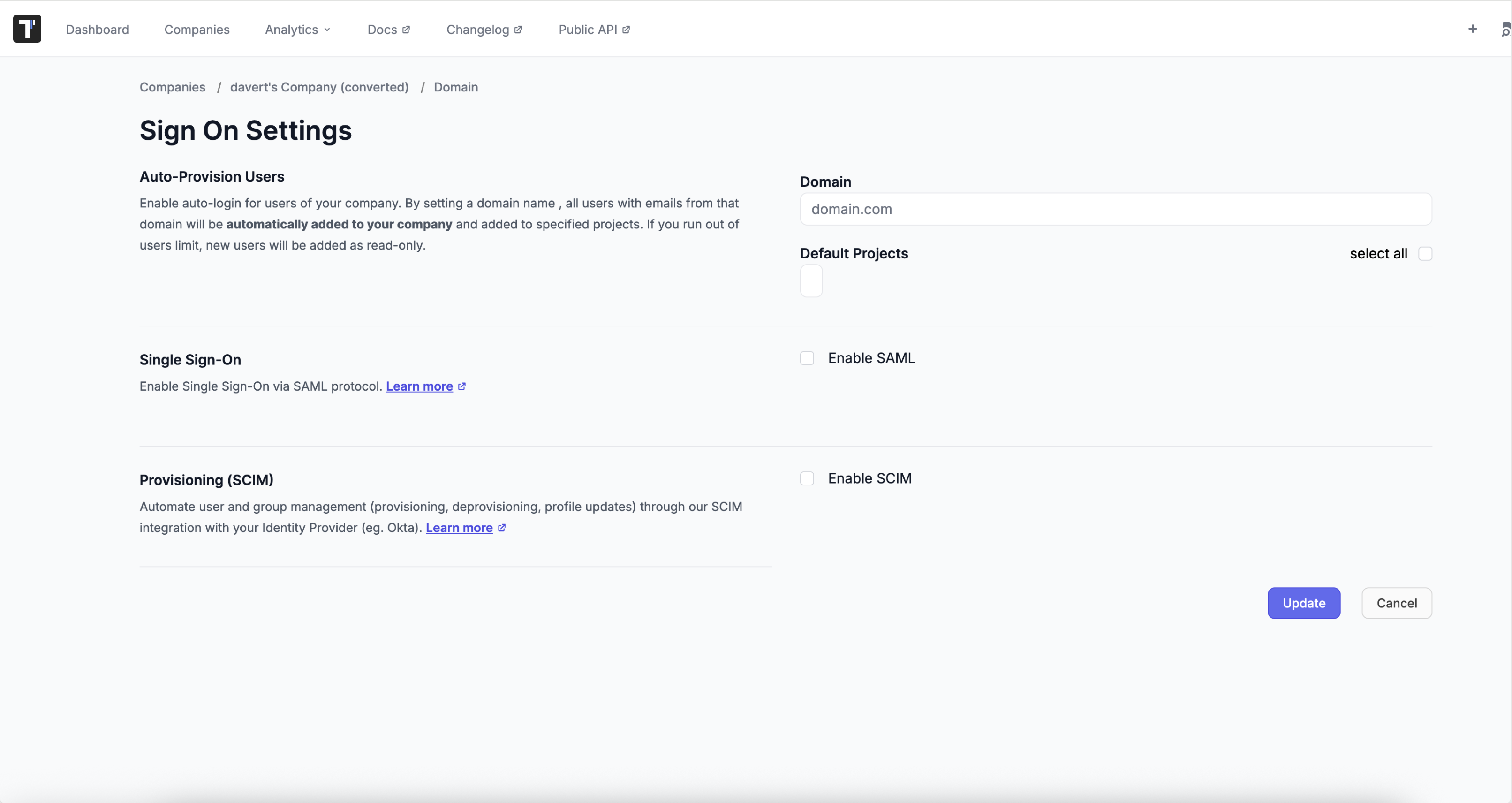
Open Testomat.io and navigate to Companies > in the Testomat.io header.
-
Click on the company where you want to enable SCIM provisioning.
-
Click Authentication in the right sidebar.
-
Select the Enable SCIM toggle to turn it on.
Generating SCIM API credentials
Section titled “Generating SCIM API credentials”After enabling SCIM provisioning, you need to generate SCIM API credentials:
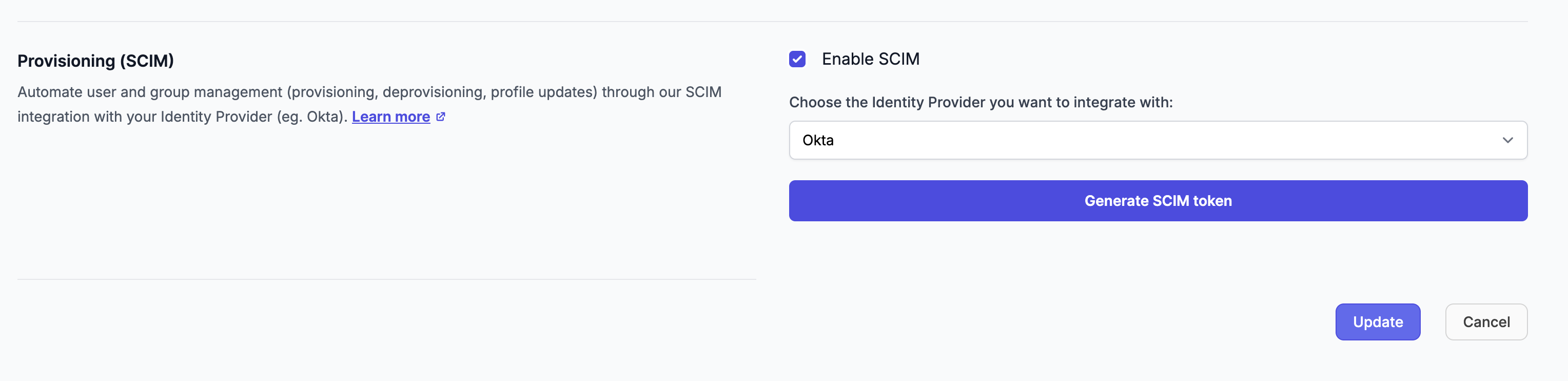
- Under SCIM Provisioning, choose Identity Provider (Okta f.e.) and click on Generate SCIM token button to generate SCIM token.
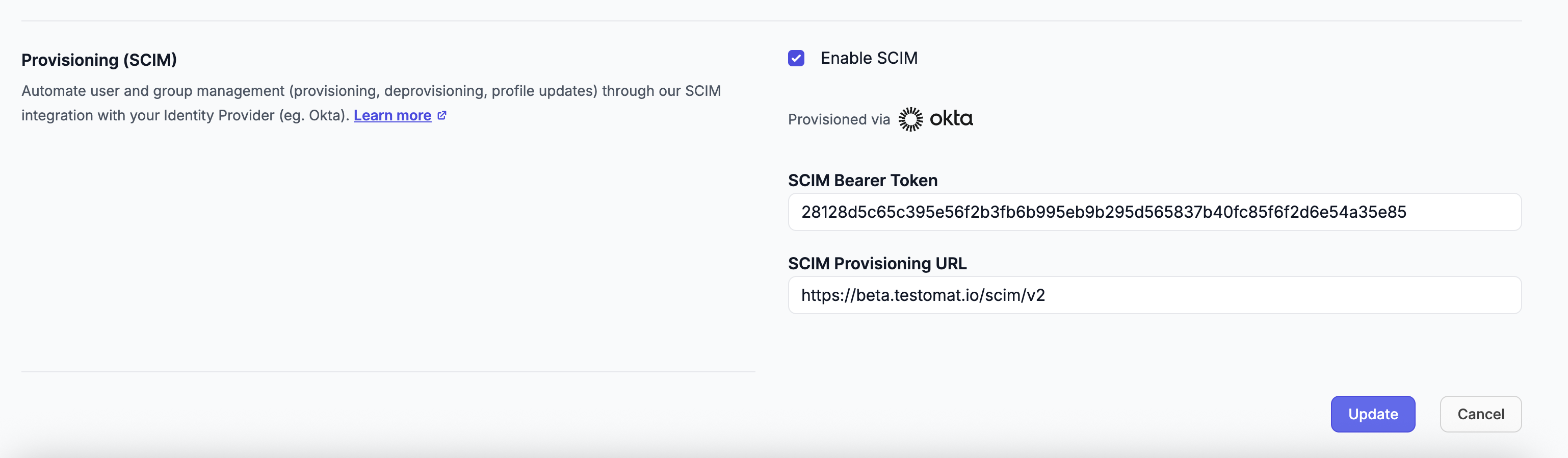
- Copy and securely store the following information:
- SCIM Base URL: This is your company-specific SCIM endpoint URL (format:
https://app.testomat.io/scim/v2) - SCIM Bearer Token: This token is used for authentication in SCIM API requests
- SCIM Base URL: This is your company-specific SCIM endpoint URL (format:
Configuring your identity provider
Section titled “Configuring your identity provider”After generating your SCIM credentials, configure SCIM provisioning in your identity provider:
SCIM API endpoints
Section titled “SCIM API endpoints”Testomat.io implements SCIM 2.0 endpoints for user and group management:
Users endpoints
Section titled “Users endpoints”GET /scim/v2/Users- List users (supports pagination and filtering)GET /scim/v2/Users/{id}- Get user detailsPOST /scim/v2/Users- Create a new userPUT /scim/v2/Users/{id}- Replace user informationPATCH /scim/v2/Users/{id}- Partially update user informationDELETE /scim/v2/Users/{id}- Deactivate a user (soft delete)
Groups endpoints
Section titled “Groups endpoints”GET /scim/v2/Groups- List groupsGET /scim/v2/Groups/{id}- Get group detailsPOST /scim/v2/Groups- Create a new groupPUT /scim/v2/Groups/{id}- Replace group informationPATCH /scim/v2/Groups/{id}- Partially update group informationDELETE /scim/v2/Groups/{id}- Delete a group
Discovery endpoint
Section titled “Discovery endpoint”GET /.well-known/scim-configuration- Returns ServiceProviderConfig with server capabilities
All SCIM requests use application/scim+json content type and require Bearer token authentication in the Authorization header.
Supported attributes
Section titled “Supported attributes”User attributes
Section titled “User attributes”Core attributes:
id- User ID (read-only)userName- Maps to user email addressname.formatted- Full name of the useractive- Boolean indicating if user is active (false deactivates user and removes access)emails[0].value- Primary email addressmeta.created/meta.lastModified- Timestamps (read-only)
Testomat extension schema:
- Schema:
urn:ietf:params:scim:schemas:extension:testomat:2.0:User testomat_roles- Multi-valued array of roles:qa,manager,billing,read
Group attributes
Section titled “Group attributes”id- Group ID (read-only)displayName- Group/team namemembers[]- Array of users in the group (containsvalue: user ID,display: user name)meta.created/meta.lastModified- Timestamps (read-only)
Limitations
Section titled “Limitations”While SCIM simplifies user management, be aware of the following limitations:
-
Attribute Mapping: Not all user attributes may be supported or mapped between Testomat.io and your IdP. Review attribute mappings to ensure accuracy.
-
Group Management: Group provisioning is supported; however, nested groups or complex group hierarchies may not be fully replicated. Group deletion is currently a destructive operation.
-
Filtering: Only the
eq(equals) operator is supported for filtering onuserName(Users) anddisplayName(Groups). Other filter operators return a 501 Not Implemented error. -
Real-Time Sync: There may be a delay between changes in the IdP and their reflection in Testomat.io, depending on synchronization schedules configured in your identity provider.
-
Password Management: SCIM does not support password synchronization or password updates.
-
Bidirectional Sync: Testomat.io does not push user or group changes back to the identity provider.
Troubleshooting
Section titled “Troubleshooting”If you encounter issues with SCIM provisioning:
- Verify that SSO is properly configured before enabling SCIM
- Ensure the SCIM Bearer Token is correctly configured in your identity provider
- Check that the SCIM Base URL matches the value provided in Company Settings
- Verify user email addresses match between your IdP and Testomat.io
- Review synchronization logs in your identity provider for error messages